Dear Friends,
“The Attack on Food and Farmers—and How to Fight Back” premieres this Friday and Saturday.
This week’s newsletter includes a link to the symposium press release, the final program, and a link to a new article by Professor David Hughes about the cognitive warfare we are facing.
I hope you enjoy it, and be sure not to miss the symposium, which is chock full of information you have not heard anywhere else.
Program: The Attack on Food and Farmers, and How to Fight Back!
September 6-7, 2024
Day 1
______________________________
11 am EDT Introduction Opening remarks by Meryl Nass, MD
________________________________________________________________________
Session 1 The general outline of the attack on food
and agriculture
11:05 am Catherine Austin Fitts Food: Freedom or famine
11:25 am Patrick Wood Food as a weapon against civilians is entering a new
phase as One Health and genetic modification are in
bloom
________________________________________________________________________
Session 2 So many ways our food supply is being
attacked
A. Poisons in our food and how they harm us
11:50 am Andre Leu, D.Sc Regenerating agriculture, from degenerative toxic industrial
agriculture to regenerative nature-based living systems –
which system will we choose?
12:15 pm Zen Honeycutt, BA Food supply expose and what we can do to be healthy
12:37 pm Michael Baum, JD A win against Roundup, followed by an audacious attempt
to end pesticide/herbicide injury litigation
1:00 pm Don M. Huber, Ph.D. Glyphosate: A betrayed trust and it's remediation
1:25 pm Stephanie Seneff, Ph.D.
Glyphosate, the ecosystem, and climate change
1:55 pm Jeffrey Smith Are GMOs and Roundup causing your disease?
2.15 pm Jeffrey Smith Existential threats from gene editing—via Food,
environment, and the microbiome
B. Industrial farming versus independent farmers
2:40 pm Breeauna Sagdal, BA Barriers to market access and liquidity for small farms
3:00 pm John Klar, Esq. The antidote to industrial agriculture is below our feet
3:20 pm John Moody Dirt poor & badly bred – what happened to all the nutrition
in our food supply?
C. Reducing available farmland
3:35 pm Brook DeLorme Transmission lines and solar panels breaking up farmland
3:45 pm Abby Rockefeller Sewage sludge is sewage sludge; it is not “biosolids"
D. Reducing high quality food and food itself
4:00 pm Brian Hooker, Ph.D. Avian influenza (bird flu)
4:20 pm Sherri Tenpenny, DO, AOBNMM, ABIHM
Vaccines in our food
4:50 pm Tracy Thurman Abolishing the Amish alternative – because it works
E. How government regulation has been used in the attack
5:15 pm Margaret Byfield, ED Assault on our land & liberty
5:35 pm Pete Kennedy, Esq. Regulatory obstacles for raw milk and local meat: efforts to
overcome them
5:55 pm Sen. Frank Niceley How we made changes in Tennessee
6:20 pm Alexis Baden-Mayer, Esq.
The farm bill & the plot to replace real farms with fake
food
F. Novel foods: bugs, lab-grown foods, synbio: transitioning the food supply
6:45 pm Robert Verkerk, BSc, MSc, DIC, Ph.D, FAC.
Why regenerative agriculture,
livestock and real meat are under attack?
7:10 pm Elze Van Hamelen, MA, MBA
Pharma food – biotech on your plate: the next
chapter in big money’s battle to end food sovereignty
Day 2
______________________________
G. Geoengineering is real, and how it is attacking food and farming
11:05 am Peter A. Kirby What is geoengineering?
J. Marvin Herndon, Ph.D.
The United Nations ENMOD treaty enabled an attack
on food, agriculture, and life
Ginny Silcox, AAS, BA, MA
Electromagnetic weather control
Session 3 SOLUTIONS: How do we fix this?
12:10 pm James Corbett The future of food is ours to decide
12:35 pm Robert F. Kennedy, Jr.
A new farm program for America
A. Growing food on the farm and in the garden – tricks of the trade
12:45 pm John Day, MD Preparing your kitchen garden
1:10 pm Mark Fulford Un-farming the farmers – to clean up the food chain and
environment.
1:40 pm Sara Woods Kender Off-grid life: Independence, resiliency, health
2:05 pm Joel Salatin The perfect patron
B. Teaching our children about farming and all that goes with it
2:15 pm Leigh Merinoff, BFA, MFA
Educating kids about farming
2:35 pm John Klar, Esq The battle over food education
C. Food sovereignty and food security
3:00 pm Richard C Cook Food sovereignty
3:25 pm Lt. Col. Tommy Waller
Food security is national security
D. Changing the rules: challenging government regulations
3:50 pm Breeauna Sagdal, BA Solutions provided through “The Beef Initiative"
4:05 pm Judith McGeary, BS The fight to block electronic tracking of our animals
E. Healing with wholesome food
4:25 pm Mark McAfee Powerful bioactives in raw milk
4:40 pm Michelle Perro, MD, DHom
Formula for change: unveiling the truth and necessity of cleaning up infant formula
5:05 pm Meleni Aldridge, BSc NutrMed PgDip CPNI Cert LTHFE
Food is medicine. But why – and how?
5:30 pm Meryl Nass, MD, John Klar, Esq, Catherine Austin Fitts
What are the most important things we just learned?
6:00 pm Meryl Nass, MD, Catherine Austin Fitts
Fixing this together: Taking Action
—————————————————————————————————————————————————————————————————————————-
Cognitive Warfare
The "Human Domain"; Cyber Tools for Controlling the Human Domain; NATO's Cognitive Warfare Doctrine; Managing the Three Camps of Awareness
By Professor David Hughes
One of the many form of attack on the human mind that has been developed over the last decade or so and overtly weaponised in 2020 is so-called cognitive warfare. My contention, fleshed out in Chapter 5 of “Covid-19,” Psychological Operations, and the War for Technocracy, is that the public’s cognitive capabilities were deliberately attacked in 2020/21. Here, I explain the origins and development of NATO’s “cognitive warfare” doctrine and how it can be used for perception management purposes.
The “Human Domain”
Cognitive warfare stems from the military concept of the “human domain,” defined by Curthoys (2014, p. 42) as “all matters pertaining to the socio-economic, partner-building, cognitive, and cultural aspects of operations,” involving “engagement and influence.” As du Cluzel (2020, pp. 36) explains, whereas the five first domains (land, sea, air, space and cyberspace) can yield tactical and operational victories, “only the human domain can achieve the final and full victory,” i.e. over the population itself.
The “human domain” originates in military documents such as U.S. Army Mastering the Human Domain: Identity Operations for Strategic Landpower (Gearty et al., 2014) and Training Humans for the Human Domain (Tatham & Giles, 2015). The latter notes that whilst experience from Afghanistan and Iraq demonstrated the importance of understanding the human domain, the lessons learned extend “far beyond counterinsurgency operations in the Islamic world.”
As it turns out, those lessons apply much closer to home, viz. the 2015 Jade Helm operation, whose slogan was “Master the Human Domain.”

Source: U.S. Army Special Operations Command (2014)
Led by Admiral William McRaven, the head of the U.S. Army Special Operations Command, Jade Helm was a massive unconventional warfare training exercise. It involved over 1,200 service personnel from three military branches deployed for eight weeks across seven U.S. states, including 17 locations in Texas alone.
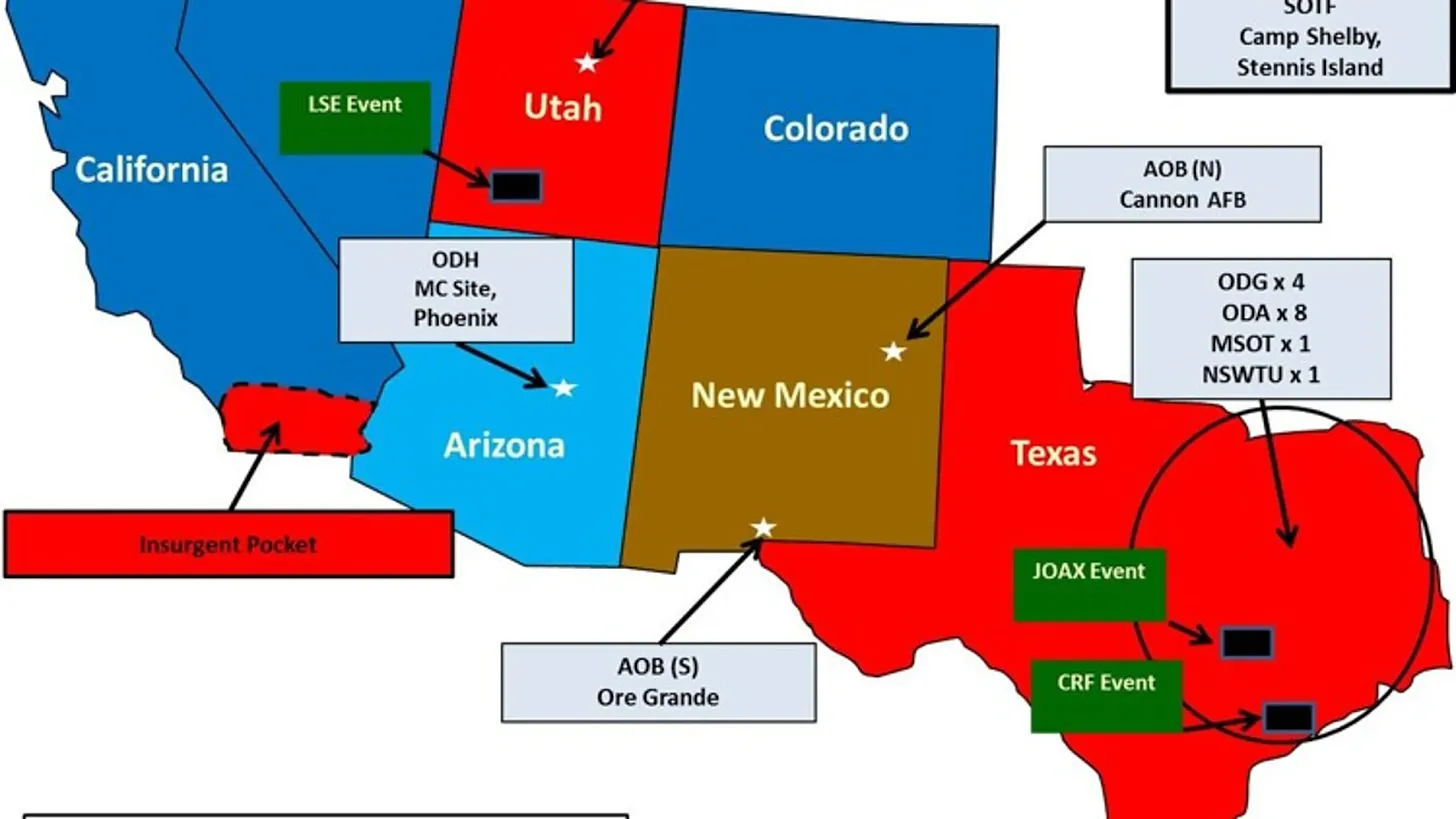
Source: U.S. Army Special Operations Command (2014)
Given that McRaven (2014, p. 28) defines the human domain as “the totality of the cultural, the ethnic, the social fabric that makes up the people that live on a particular area,” the choice of familiar home territory for Jade Helm seems strange to say the least, unless it is ultimately the domestic population itself which is to be targeted for counterinsurgency operations, consistent with the logic of the Omniwar.
Cyber Tools For Controlling the Human Domain
We know from the UK Government Communications Headquarters’ (GCHQ) Joint Threat Research Intelligence Group (JTRIG) that intelligence agencies were looking in 2011 at “compiling psychological profiles based on information available about the individual on the internet so that those conducting online HUMINT [human intelligence] operations can compile and exploit such profiles” (Dhami, 2011). So-called “psychographics” involves harvesting data about every area of an individual’s life to produce a psychological profile that allows A.I. to aim targeted messaging at specific individuals (Corbett, 2017).
Facebook was deliberately designed to generate “short-term, dopamine-driven feedback loops,” e.g. through receiving “likes” and notifications, as Chamath Palihapitiya, Facebook’s vice-president for user growth until 2011, admitted in 2017 (cited in Wong, 2017). This means that social media and similar platforms have a chemically addictive quality. Much as slot machines are designed to keep the user pulling the lever, those platforms use algorithms to keep users scrolling, engaging, and coming back for more.
The result is painfully evident from large numbers of people glued to their smartphones in public, or in social contexts where face-to-face conversation would be appropriate. A great many people appear unable to be without their smart device at any time of the day or night. The addictive quality of the apps and the devices means that people are constantly feeding their personal information into the Big Tech machine that is inseparable from the intelligence agencies (Corbett, 2019d).
Such people are “an easy target” for cognitive warfare (du Cluzel, 2020, p. 7), for they are constantly being programmed, e.g. via the kind of information that does and does not appear in their news feeds. As Palihapitiya put it: “Your behaviors, you don’t realize it, but you are being programmed” (cited in Wong, 2017).
Huxley (1958, p. 38) refers to the propaganda technique of persuasion by association. The idea is that key words are paired with other words and phrases which create a positive or negative impression as desired, and those pairings are then repeated as often as possible to create unconscious associations in the minds of the public. Classic examples in our own time include “Islamic” + “extremist” and “vaccine” + “safe and effective.” The new digital technologies allow this process to be automated. For example, Word2vec, patented in 2013 by a team of Google researchers led by Tomas Mikolov, uses natural language processing to create vector representations of words. Words that are often paired together, or used in similar contexts, appear closer together on the vector representation than words that do not. It then becomes possible, through A.I., to manipulate online content such that the desired word vectors are created.
Between 2013 and 2016, the British data analytics firm, Cambridge Analytica, used an app called “This is Your Digital Life” to collect the personal data of an estimated 87 million Facebook users without their informed consent. The data was used to create psychographic profiles on users, which in turn were used to create personalized political advertising on online platforms for the Ted Cruz and Donald Trump 2016 presidential campaigns.
The Cambridge Analytica scandal is a good example of Fitts’ (2022) notion of control being exercised one person at a time, in a cost-effective manner. For example, in a section titled “Hacking the individual,” NATO Innovation Hub manager, François du Cluzel (2020, p. 7), writes:
The revolution in information technology has enabled cognitive manipulations of a new kind, on an unprecedented and highly elaborate scale. All this happens at much lower cost than in the past, when it was necessary to create effects and impact through non-virtual actions in the physical realm.
In this context, it is intriguing to draw a contrast between “9/11” as a kinetic and highly resource-intensive act of false flag terrorism and later allegations, from around 2012 (Sandy Hook) and 2013 (the Boston Marathon incident) on, that certain major terrorist attacks have been staged (Hall, n.d.; Davis, 2024). After all, why carry out real false flag attacks, leaving real evidence to be pursued by real relatives of real victims, when cognitive warfare can be used to convince the public that the attacks are real? As Orwell (1984, p. 225) wrote, “If both the past and the external world exist only in the mind, and if the mind is controllable – what then?”
A 2023 U.S. Naval College report on cognitive warfare refers to “the use of psychology and advanced technologies to target individuals or groups precisely” (MacDonald & Ratcliffe, 2023). Disruptive ICT has made it possible to identify millions of individuals, profile them psychographically, and target their cognition. A simple example is Netflix recommending to individual users what they should watch: digital TV is not for the masses, it is customized to individuals. But when news feeds, comment sections, content recommendations, etc. are all algorithmically manipulated, an individual’s sense of reality can be massively distorted.

U.S. Naval College visualization of cognitive warfare (MacDonald & Ratcliffe, 2023)
A.I. can be used to “kettle” social media users into silos, whereby they are predominantly exposed to information that confirms their own worldview. Different groups of people experience different social realities, and society becomes divided, unable to unite against the technocrats seeking to achieve total social control.
Because of the scale on which cognitive manipulations are carried out, it might appear that we are dealing with a form of mass manipulation similar to 20th century propaganda. NATO (n.d.), for instance, claims that because cognitive warfare is “designed to modify perceptions of reality, whole-of-society manipulation has become a new norm, with human cognition shaping to be a critical realm of warfare.” In practice, however, that “whole-of-society” manipulation is achieved one person at a time and not via mass messaging.

NATO’s (n.d.) visual representation of Cognitive Warfare
Another distinguishing feature of cognitive manipulation, compared to traditional propaganda, is that it is not simply about imposing particular ideas and behaviors, but, rather, modifying cognition, i.e., “influencing the process by which we ourselves arrive at ideas, insights, beliefs, choices and behaviors” (van Hamelen, 2022). In other words, it is not just about influencing what we think, but how we think (du Cluzel, 2020, p. 8).
A simple example is TikTok, whose short videos work to reduce the attention span of users, as well as their ability to absorb long-form content and their ability to make “big picture” connections. Ever fewer people seem able to read a real book cover to cover. The outsourcing of thinking and memory to GPS, autocorrect, calendar alerts, calculators, etc. creates a “long-term process of disabling connections in your brain” (du Cluzel, 2020, p. 16).
NATO’s Cognitive Warfare Doctrine
It is telling that cognitive manipulation yields to NATO’s “cognitive warfare” doctrine in 2020, the year the Omniwar began. From this point on, an overtly destructive aspect is introduced along with language of the “enemy”:
Cognitive warfare is thus an unconventional form of warfare that uses cyber tools to alter enemy cognitive processes, exploit mental biases or reflexive thinking, and provoke thought distortions, influence decision-making and hinder actions, with negative effects, both at the individual and collective levels (Claverie & du Cluzel, n.d., p. 2).
The U.S. Army Special Operations Forces (2008, pp.1-2) defines unconventional warfare (UW) as “Operations conducted by, with, or through irregular forces in support of a resistance movement, an insurgency, or conventional military operations.” Examples of UW cited include U.S. support of the Contras in Nicaragua and the mujahideen in Afghanistan in the 1980s. In other words, we are dealing with illegal subversions of society.
A key objective of cognitive warfare is “undermining trust (public trust in electoral processes, trust in institutions, allies, politicians…)” (du Cluzel, 2020, p. 8). The Cambridge Analytica scandal looms large here. This process of undermining trust, du Cluzel continues, has the “potential to unravel the entire social contract that underpins societies.” That, however, is precisely the point of the Omniwar, i.e. to destroy centuries of liberal tradition and replace it with global technocracy.
Unlike in traditional propaganda, individuals subjected to cognitive warfare are not merely passive recipients of certain kinds of messaging, but, rather, actively help to drive the messaging themselves through social media and other forms of online participation. In that respect, “the individual becomes the weapon” (du Cluzel, 2020, p. 8). This is consistent with the general principle that if we do not actively resist in the Omniwar, we ourselves become weaponized and turned into instruments of our own oppression.
Knowledge of how to manipulate these processes, du Cluzel told a NATO panel discussion on October 5, 2021, “is easily turned into a weapon” (cited in van Hamelen, 2022). For example, the rational discussion and debate that is necessary for democracy to work is rendered impossible by the “echo chambers” created by A.I. algorithms. A “society” composed of people experiencing different social realities – and rendered unable to know reality in the first place by “deep fake” technology – cannot function democratically and can only be managed technocratically.
The official literature pins the blame for cognitive warfare and attempts to disrupt democracy on Russia and China (MacDonald & Ratcliffe, 2023), meaning that the United States “cannot afford to be on the back foot” when it comes to developments in CW (du Cluzel, 2020, p. 31). This is the same model that was used during the Cold War to justify the MKULTRA programme, bioweapons development, massive stockpiling of nuclear weapons, etc. The “official enemy” pretext is always used to conceal the nefarious activities of the deep state, which are now being weaponized against Western populations.
According to NATO (n.d.), cognitive warfare involves “attacking and degrading rationality” and becomes “increasingly complex as non-military targets are involved.” In other words, it is about attacking the rationality of the citizenry. What I have called “cognitive attack” against the population was a defining feature of the “Covid-19” psychological operation (Hughes, 2024a, Chapter 5).
Furthermore, if “cognitive warfare’s objective is to make everyone a weapon” and to “harm societies” (du Cluzel, 2020, pp. 25), this was achieved during the “Covid-19” operation, when the majority of society was manipulated into attacking the minority to make it conform with draconian dictats (Hughes, 2024a, Chapter 7). The resultant social cleavages, spoiling relationships of all kinds, run deep.
NATO (n.d.) includes lawfare under the cognitive warfare category. Recent attempts to use lawfare to close down questioning of alleged false flag terrorist incidents are therefore notable, e.g., in the case of Sandy Hook (Alex Jones) and the Manchester Arena attack of 2017 (Richard D. Hall [see Davis, 2024]). NATO, it should be remembered, has a known history of committing false flag terrorism (Hughes, 2024b, pp. 92-95).
Three Camps of Awareness
Cognitive warfare can also be used for perception management purposes.
In line with DARPA’s (n.d.) promotion of “strategic narratives” and techniques of perception management dating back at least as far as “9/11,” there appear to be at least three camps of awareness when it comes to controlling the “Covid-19” narrative. The first camp is the official narrative, as espoused by mainstream everything; it is based on Big Lies, yet is believed by a dwindling majority susceptible to the power of propaganda.
The second camp is for those who have doubts about Camp 1, but are met by a battalion of fake dissidents whose role it is to make sure that critical debate and discussion never strays beyond certain parameters, in this case a public health/pharmaceutical/medical paradigm. The fake heroes are recognisable by their large numbers of followers, their ability to survive and prosper on mainstream platforms, the implausible amount of content they are able to put out while flying around the world from one event to the next, their cross promotion of one another’s work, their ostracization of those in Camp 3, and their refusal to look seriously at certain key evidence (viz. Project Veritas’ refusal to pursue the issue of “Covid-19 vaccine” contents).
Camp 3 is the truth. It attracts the most serious truth seekers, whose reach on mainstream platforms is severely restricted. Relative to Camp 2, Camp 3 is tiny, which is testimony to the success of the perception management campaign. In the case of “Covid-19,” its hallmark is an ability to get to the underlying social relations producing the narratives in the first two camps, recognizing in particular the central role of the military and the technocratic and transhumanist agendas at work. Camp 3 is an even more challenging place to get to, intellectually and psychologically, than Camp 2, because it requires an unwavering commitment to the truth, more rigorous research, a willingness to endure personal sacrifices, and an ability to face the true horror of what is taking place in the world.
Cognitive warfare uses algorithms to amplify the messages of Camp 1 to those in Camp 1, and the messages of Camp 2 to those in Camps 2 and 3, while suppressing the content of those in Camp 3. Through this technique, those in Camps 1 and 2, trapped in their echo chambers, become increasingly convinced of the veracity of their own positions, which they themselves then actively promote. They are unlikely to pierce the veil of deceit that has been woven for them.
References
- Claverie, B., & du Cluzel, F. (n.d.). The cognitive warfare concept. NATO Innovation Hub. https://innovationhub-act.org/wp-content/uploads/2023/12/CW-article-Claverie-du-Cluzel-final_0.pdf.
- Corbett, J. (2017, July 2). Psychographics 101. The Corbett Report. https://corbettreport.com/psychographics-101/.
- Curthoys, K. (2014, January 6). The Army in 2014. Army Times. https://www.documentcloud.org/documents/2075518-nexis-human-domain.html#document/p28/a216990.
- DARPA. (n.d.). Narrative networks. https://www.darpa.mil/program/narrative-networks
- Davis, I. (2024). The Manchester Attack. Independently published. https://iaindavis.com/sfcz9nrjt/.
- Dhami, M.K. (2011, March 10). Behavioural Science Support for JTRIG’s (Joint Threat Research and Intelligence Group’s) Effects and Online HUMINT Operations. Joint Threat Research Intelligence Group. https://www.statewatch.org/media/documents/news/2015/jun/behavioural-science-support-for-jtrigs-effects.pdf.
- du Cluzel, F. (2020, June-November). Cognitive Warfare. NATO Innovation Hub. https://innovationhub-act.org/wp-content/uploads/2023/12/20210113_CW-Final-v2-.pdf.
- Fitts, C.A. (2022, January 14). Control is one person at a time. Solari Report. https://home.solari.com/control-is-one-person-at-a-time/.
- Gearty, D.L., Sproul, T., McMurtrie, R., Munn, C., Boyd, J., & Castleman, E. (2014). U.S. Army Mastering the Human Domain: Identity Operations for Strategic Landpower. U.S. Army. https://publicintelligence.net/us-army-identity-operations/.
- Hall, R.D. (n.d.). Manchester Attack. https://www.richplanet.net/manchester.php.
- Hughes, D.A. (2024a). “Covid-19,” Psychological Operations, and the War for Technocracy. Palgrave Macmillan.
- Hughes, D.A. (2024b). Wall Street, the Nazis, and the Crimes of the Deep State. Skyhorse.
- Huxley, A. (1958). Brave New World Revisited. Harper & Row.
- MacDonald, A., & Ratcliffe, R. (2023). Cognitive Warfare: Maneuvering in the Human Dimension. Proceedings of the U.S. Naval Institute. https://www.usni.org/magazines/proceedings/2023/april/cognitive-warfare-maneuvering-human-dimension.
- NATO. (n.d.). Cognitive Warfare. https://www.act.nato.int/activities/cognitive-warfare/.
- Orwell, G. (1984). Nineteen eighty-four. Oxford University Press.
- Tatham, S., & Giles, K. (2014). Training Humans for the Human Domain. United States Army War College Press. https://press.armywarcollege.edu/monographs/435/.
- U.S. Army Special Operations Command. (2014). Request to Conduct Realistic Military Training (RMT) JADE HELM 15. https://www.documentcloud.org/documents/2075511-jade-helm-15-presentation.html.
- U.S. Army Special Operations Forces. (2008). Unconventional Warfare. https://irp.fas.org/doddir/army/fm3-05-130.pdf
- van Hamelen, E. (2022, September 22). Citizen’s Brain Is the Battlefield in 21st-century Warfare. Global Research. https://www.globalresearch.ca/citizen-brain-battlefield-21st-century-warfare/5794156
- Wong, J.C. (2017, December 12). Former Facebook executive: social media is ripping society apart. The Guardian. https://www.theguardian.com/technology/2017/dec/11/facebook-former-executive-ripping-society-apart.








